Contract Change Control System technique is used under the process Control Procurements.
I know many of you must be aspiring to become successful project managers in your career which can be the stepping stone to become good leaders. How you can achieve this? Yes, by implementation which is critical. And to distinguish from others you need to have some kind of credentials which can be obtained through certifications like PMP, ITIL. To know more about or to get prepared for the same, you can always approach me @ bksprasad@yahoo.com or subramanya.bks@gmail.com
Thursday, March 31, 2016
Contract Change Control System
Wednesday, March 30, 2016
Procurement Negotiations
The project manager should involve other project management team while negotiation with seller so that it will assist in understanding the technical, quality and management requirements.
Also Procurement Negotiations are used if any disputes, outstanding issues, claims during the closing of procurements. If this is not working, one can use Alternative Dispute Resolution (ADR) through mediation. In the worst case it has to be settled in the court which is least preferred.
At the end of the day the Procurement Negotiations should be from win-win proposition.
Procurement Negotiations technique is used under the processes Conduct Procurements and Close Procurements.
Tuesday, March 29, 2016
Advertising
Advertising technique is used the process Conduct Procurements.
Independent Estimates
For example if the bidding price is $20K and our estimation is $15k, this is a considerable gap. The reasons can be either the scope understanding from the seller side is incorrect or the buyer has not done his estimate properly.
Independent Estimates techniques is used the process Conduct Procurements.
Wednesday, March 23, 2016
Proposal Evaluation Techniques
Proposal Evaluation Techniques is used the process Conduct Procurements.
Tuesday, March 22, 2016
Bidder Conferences
Bidder Conferences technique is used the process Conduct Procurements.
Monday, March 21, 2016
Market Research
Market Research technique is used under the process Plan Procurement Management.
Sunday, March 20, 2016
Make-or-Buy Analysis
Sometimes the budget constraints also influence make-or-buy decisions. In either case we need to consider both direct and indirect costs. Also once we decide on buy decision the type of contracts need to be considered based on the risk sharing between the buyer and seller.
The Make-or-Buy Analysis results in Make-or-Bye Decisions.
Make-or-Buy Analysis technique is used under the process Plan Procurement Management.
Thursday, March 17, 2016
Technical Performance Measurement
Technical Performance Measurement technique is used under the process Control Risks
Wednesday, March 16, 2016
Risk Audit
Tuesday, March 15, 2016
Variance and Trend Analysis
Variance and Trend Analysis technique is used under the process Control Risks.
Monday, March 14, 2016
Risk Reassessment
Risk Reassessment technique is used under the process Control Risks.
Friday, March 11, 2016
Contingent Response Strategies
Contingent Response Strategies technique is used under the process Plan Risk Responses.
Thursday, March 10, 2016
Strategies for Negative Risks or Threats and Strategies for Positive Risks or Opportunities
Avoid is used when you don’t want to get into the situation. Example: avoiding the scope, extending the schedule, changing the strategies and even avoiding the project itself. This response is used when the risk ranking is high with high probability and high impact.
Transfer is shifting the risk to some other party. By transferring the risk means not disowning the risk. Still the project team owns the risk but usually transfer from the financial angle. For example Insurance, bonds, warranty, guarantee or even transferring some of the work/scope back to the customer. This response is used when the risk is at lower ranking.
Mitigation is reducing the probability and/or impact to the situation. For example providing the training to the staff when there is no expertise available, having the standby machines when the primary fails. This response is used when the risk ranking is high with high probability and high impact.
Accept is acknowledge the risk and don’t take any action till it materializes. There are two types of acceptance. One is passive and second is active acceptance. Passive acceptance is don’t do anything. When it happens then get into action. For example you know that machine is going to be down. When goes down then only you will try to get another one or repair it. Active acceptance is preparing for contingency reserve in terms of cost, schedule or resource. This response is used when the risk is at lower ranking.
Exploit is used to realizing the opportunities. For example early delivery to get more business, use latest technology to save cost. Here the team ensures that risk materializes and the response is in an aggressive manner.
Share is allocation of entire or partial risk to some other third parties to gain benefits. For example joint venture, partnership.
Enhance is increasing the possibility of occurrence of risk by increasing the probability and or impact. This is similar to Exploit but not in an aggressive way. For example, adding the resources to complete the project early.
Accept is taking the opportunity if it occurs, but not activity pursing it.
Strategies for Negative Risks or Threats and Strategies for Positive Risks or Opportunities techniques used under the process Plan Risk Responses.
Wednesday, March 9, 2016
Quantitative Risk Analysis and Modeling Techniques
Sensitivity analysis is used when we change any of the variables what can be the impact on the end result. The most common diagram used under Sensitivity analysis is Tornado diagram. It is a bar chart to compare the relative importance of the variables. The y- axis consists of different risks and the x axis represents uncertainties for range for each of these risks in the form of bar chart and is drawn from highest length to the lowest length of the bars.
Expected monetary value analysis helps in finding which is riskier by comparing two different scenarios. For example is it worth to buy equipment or build on your own. The calculation is based on initial investment, probability and impact. The higher the value better is the option.
Modeling and simulation technique uses Monte Carlo simulation analysis by choosing the random values for each iteration and provides what should be the contingencies for every risk.
Quantitative Risk Analysis and Modeling Techniques is used under the process Perform Quantitative Risk Analysis.
Sunday, March 6, 2016
Data Gathering and Representation Techniques
An interview is to gather information from experts based on historical information. While collecting the probability and impact there may be situation stakeholders having difference of opinion. For example for a particular risk one may say the probability is 20%, the other stakeholder may say the probability is 40% and one more stakeholder may say it is 80%. So we can use three point estimation (PERT) to arrive the more approximate or realistic value. Similarly it is applicable for Impact.
Probability distribution uses two types one is Beta distribution and the second is Triangular distribution. These distributions provide the relative likely hood of risks in terms of cost and time.
Data Gathering and Representation Techniques is used under the process Perform Quantitative Risk Analysis.
Saturday, March 5, 2016
Risk Urgency Assessment
Risk Urgency Assessment technique is used the process Perform Qualitative Risk Analysis.
Friday, March 4, 2016
Risk Categorization
Risk Categorization technique is used under the process Perform Qualitative Risk Analysis.
Thursday, March 3, 2016
Risk Data Quality Assessment
Risk Data Quality Assessment technique is used under the process Perform Qualitative Risk Analysis.
Wednesday, March 2, 2016
Probability and Impact Matrix
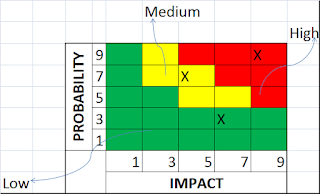
Probability and Impact Matrix technique is used under the process Perform Qualitative Risk Analysis.
Tuesday, March 1, 2016
Risk Probability and Impact Assessment
Once you identify the risks we can’t address all the risks with same priority. One needs to assess the probability and Impact by using the scaling. For example probability with >80% can be of higher scale and <10% can be in the lower scale. Similarly for the impact we can use the scaling factor. If the impact is >$40K then scaling is high <$5K the scaling low. The definitions of these scales are defined as part of Risk Management plan. By using this one can arrive the risk priorities like high, medium, low…
If the risk ranking is low it should be kept as watch list.
Risk Probability and Impact Assessment technique is used under the process Perform Qualitative Risk Analysis.